In a recent conversation with Anthony Besett of GetWireless, a metaphor emerged: a network is not just a collection of devices, but an ecosystem. The line is as catchy as it is directional: original equipment manufacturers (OEMs), a foundational contributor to global supply chains, have a growing responsibility for securing today’s interconnected environments early in design.
How did we get here?
Well, we live in a connected world. According to IoT Analytics, which tracks and analyzes IoT connectivity, the number of connected IoT devices will grow 14% by end of 2025, reaching 39 billion in 2030 and more than 50 billion by 2035. That’s six devices for every single person on earth.
Another way to frame this: 73.2% of the world’s population accesses the internet. A parade of innovative technologies have arrived: artificial intelligence (AI) infrastructure, hyperscalers (developers scaling data center networks), quantum computing, and the data center surge. Deloitte ranks “cyber and/or physical security concerns” as number three on its list of data center infrastructure challenges, tapping OEMs on the shoulder to take note of technology’s evolving impact.
Besett serves as Vice President OEM Embedded Solutions for GetWireless, a leading value-added distributor of cellular solutions like intelligent gateways, servers, asset trackers, modems, and other solutions for IoT applications. Besett predicts that OEMs focusing only on designing, making, and selling products may be shortsighted. IoT devices are increasing and networks are becoming more complex. The stakes for robust, holistic security have never been higher – and OEMs recognizing that their products are responsible for the entire network ecosystem will be the ones to differentiate their product.
Intentional security for OEMs is a bold leap forward for customers.
Beyond Silos: A Network as a Secure Ecosystem
Besett emphasized that traditional approaches to security often focus on isolated components, protecting a gateway here or running penetration testing (pen testing) there. He says, “We have to be paying attention to security across the entire infrastructure, not just one piece of it. Historically, you’ve seen there’s attention to one piece.”
Many of GetWireless’s suppliers do pen testing, for example, but Besett sees that changing in the future with security-minded solutions that are guaranteed to protect networks and all the devices that go beyond that point.
Here’s why: in an ecosystem, every element is interdependent. A vulnerability in one device – like a sensor, workstation, or camera – threatens the health of the entire network. Just as the rapid spread of Dutch Elm Disease endangers a forest, a single weak link in a network can compromise an entire digital environment. As an example, consider the Mars Hydro breach. The China-based maker of LED grow lights had 2.7 billion records exposed, including passwords, IP addresses, and device IDs, all because the attacker was in Wi-Fi range.
OEM manufacturers have an opportunity to help mitigate the risks of IoT data breaches. Besett shares, “I was in a conversation not too long ago where a customer’s whole network was hacked because somebody plugged into a gateway that wasn’t controlled. And so now you’ve got a hole. There are lawsuits. It’s going to be a mess.” He says fragmented security leaves the entire network ecosystem exposed.
The takeaway for cybersecurity: silo thinking is risky when it comes to individual OEM network products. A piecemeal approach is no longer sufficient.
Zero Trust Security and Zentry
Besett points out the value of zero-trust architectures, such as the FreeWave Zentry™ solution. Referencing back to his customer example, he explains, “There were vulnerabilities there that if something like Zentry was on that, that wouldn’t have happened because they (the attacker) would have actually had to request access.”
“The devices on the edge, sensors, the workstations, the PCs, the tabs, the LPRs, all those different things, they get security as well. And it’s really cool because Zentry controls who has access, when they have access, and exactly what they have access to. What’s so unique about Zentry and their kind of ‘look’ on the infrastructure is . . . giving the control to an OEM to be able to secure everything for their customers, not just one piece.”
Security must extend to every part of the network ecosystem, he says. It’s not enough to lock the front door; every window, back door, and fence line needs protection.
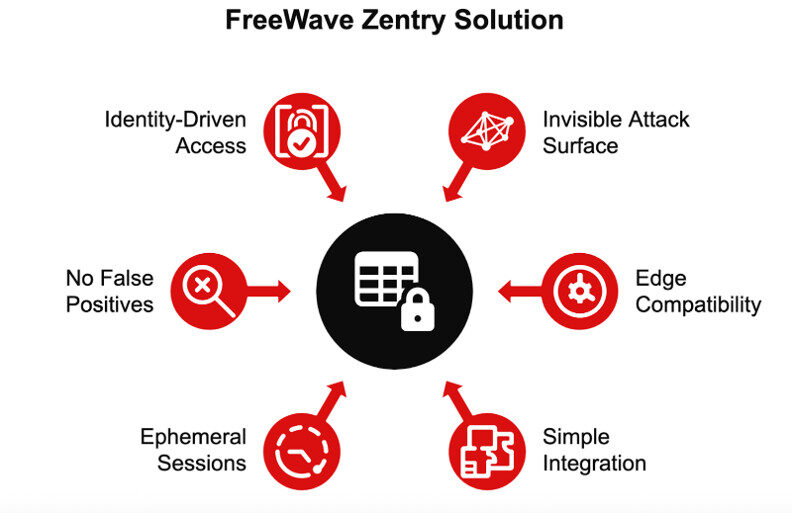
The FreeWave Zentry solution secures not just one component but the entire deployment by making the attack surface invisible – there are no public IP addresses, open ports, or static tunnels to scan or exploit. Ephemeral sessions mean access appears only when needed and disappears when complete, leaving no standing exposure. Deterministic control removes noise, helping small security teams focus on real threats without wasting time on no false positives.
Besett explains, “Zentry controls who has access, when they have access, and exactly what they have access to.” This Identity-driven access ties every connection to a verified user, device, and policy for precise control. Devices, from license plate readers to medical wearables, become ubiquitous and integral to securing critical operations. At GetWireless, Besett says the company looks at the entire connected world, including body wearing devices, POS machines, monitoring cameras, and weather stations. “We’re engaged at all those different levels in the community,” he says.
Security, according to Besett, is no longer a “nice-to-have” but a fundamental requirement for any device that connects to a network. He notes, “Do you want to be the hole in the network that creates the problem for a customer or brings down a network?” The risks are real, from lawsuits to national infrastructure threats. Zero trust gives OEMs an opportunity to proactively address vulnerabilities at every layer, not just at the gateway or a single device, but across the entire ecosystem.
What OEMs Need to Know About Zero Trust
Security is poised to become a differentiator in the marketplace. With many devices becoming commoditized, Besett suggests that embedding zero trust could set OEM network products apart.
Besett asks a good question: “Why would you choose a device that doesn’t meet these requirements to deploy out there?” Security, when built in from the design phase (called Secure by Design) then becomes both a technical feature and a revenue opportunity. He suggests:
Make security a priority from the outset. Don’t leave it as an afterthought.
Consider the entire ecosystem, not just your own device.
Educate your customers and partners about the importance of holistic security.
Stay ahead of threats by embedding solutions like zero trust that minimize human error and close backdoor vulnerabilities.
Among OEM’s chief concerns are time-to-market and complexity. Here, the FreeWave Zentry solution delivers. Built for the rugged Razor’s Edge, Zentry works seamlessly in OT, IoT, and disconnected environments where most zero trust tools cannot operate. Integration is simple. Zentry works alongside existing security operations center (SOC), security information and event management (SIEM), and firewall tools without complex reconfiguration.
Next Steps
As GetWireless pilots proof-of-concept deployments with the FreeWave Zentry solution across multiple gateways and devices, Besett sees a future where security is foundational, not optional.
“More and more, it’s being brought forward to the attention of OEMs how vulnerable our nation and individual networks are. I’ve been engaged with FreeWave . . . it looks at the whole infrastructure, not just one piece of it. It’s beautiful.” A device as simple as a TV or license plate, Besett says, could be backhauling sensitive information about location and listening in on audio.
“If you have devices that give you security and also include communications,” Besett adds, “you’re going to win faster. Everybody in the ecosystem wins.”
Every device, connection, and user plays a role in the health of the whole.
Besett says, “It (security) has to be designed from the ground up. We have to be thinking about those things and have the ability to do that.” He adds, “It’s time for these different security leaders . . . to move past legacy solutions and consider a complete IoT lifecycle approach.”
In a connected world, OEMs have an opportunity to protect the entire network using a zero-trust approach, intentional design, and a new way of thinking about security resilience for the entire network ecosystem.