Actor John Krasinski plays Jim Halpert in The Office. Jim’s one-liners pave his pursuit of a fulfilling sales career at Dunder Mifflin, a paper company. (Example: I am about to do something very bold in this job that I’ve never done before: try.)
Spoiler alert: Krasinski becomes one of the company’s top salespeople. That’s what human beings do. We evolve. So does technology.
Today, industrial internet of things (IIoT) data demands devices that are dynamic because, like Krasinski’s character, networks are continuously evolving.
The goal? Make your network and devices resilient.
In this blog, we’ll explore the number one problem for cellular network industrial users, what you should know about static and dynamic IP (Internet Protocol) addresses, how they impact network security, and a true story of how we hacked into a customer’s network – during a meeting with them.
——————————————————————————–—-
What are Static and Dynamic IP Addresses? Why Should You Care?
Let’s start with the basics. An IP address is a string of numbers identifying each device connected to a network. The Internet Service Provider (ISP) assigns the unique device “name” allowing it to:
- Be recognized by the network (hey, I see you)
- Communicate with other devices (let’s talk)
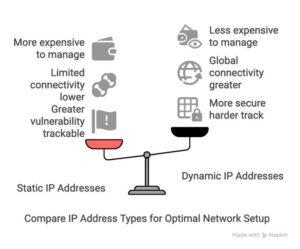
Historically, industrial devices use static IP addresses. From web servers to sensors to VPNs, these addresses are fixed. They never change. It’s kind of like living at the same house address all your life – when people know where you live, they can send you whatever mail they want, whenever they want.
In contrast, dynamic IP addresses get assigned a unique address by the Dynamic Host Configuration Protocol (DHCP) server. Every time a router reboots or the system changes or said device is not in use, the device’s IP address changes. In this case, imagine living in Paris one day and Milan the next. With no one knowing your address, you are free from receiving junk mail forever.
In the Age of Connectivity – where devices, data, and business scenarios are constantly in flux – are static IPs a liability for industrial users?
Why do Industrial Companies Use Static IP Addresses?
In short: dependable network access. Businesses need consistent destinations for sending data and a stable address to connect to. Dynamic IP addresses, which shift over time, complicate this process. For a clearer picture, think of how tricky your search for information would be if Google’s website address kept changing.
While consistency has been the reasoning behind static IP addresses, technology has evolved – and so has cyberattacks. The vulnerability of static IP addresses now outpaces their original usefulness.
Unidirectional vs. Bidirectional Integration
Most cellular devices are designed with unidirectional integration where information travels one way. For industrial users, this means data from the edge travels to the world. Many cellular devices are not factory-equipped with a bidirectional, or two-way, data path.
A garage door sensor with unidirectional data, for instance, only gets you so far. If you put your bike away, but forgot to close the garage door, an alert notifies you. It’s now Sunday morning so you’re home and can close it as you get your morning coffee going. It doesn’t work, though, if you’re on a flight to Turks and Caicos (although an open garage door probably wouldn’t ruin your vaca).
A better way would be an app where you click a button and close the door, and it’s confirmed on your phone. This way, you have a secure home no matter where you are.
The same scenario holds true for industrial use cases. Bidirectional data allows you to turn devices – like pumps, drives and machinery – on and off to prevent failures and save time driving to remote places.
What is the cost of an oil spill for an hour or productivity loss because machinery is down or, most importantly, equipment failure that triggers unsafe conditions?
Devices with bidirectional integration lead to greater data accuracy and data accessibility across the enterprise. In a connected world, data democratization gives people insight to make smarter decisions and be more productive.
For example, when a project manager and a safety engineer access the same real-time data, rather than work in data silos, system integration creates more efficient workflows. Shared data, connected “things,” and different platforms work together. Cellular devices with a bidirectional data path help integrate a project management platform with safety data. Imagine watching an HMI (human-machine interface) screen to monitor a pump’s pressure, temperature, flow rate and vibration. The screen flashes red, indicating high pressure and overheating. You’re able to hit the off button, eliminating a potential explosion. Every second counted and with bidirectional data, you averted disaster.
Think of it this way: unidirectional data brings “problems” to you with no simple button to fix them. Stressful. Bidirectional data brings “problems” to you and the ability to solve those problems. Peaceful.
One solution, however, begets more issues. At each end of the connection, there is an IP address or, put another way, a fresh opportunity to hack your network.
Top Concern: Security Breaches
Have you ever had a conversation involving IoT where security wasn’t part of the discussion? The answer, most likely, is no.
With the continued rise of IoT devices on the network, the news platform Sci-Tech Today estimates that around 33% of attacks on IoT devices may impact critical operations, followed by 32% lack of skilled personnel to implement IoT security.
Dynamic IPs can create greater network resilience because they simplify network administration and they typically experience fewer errors.
Two words: be prepared.
In our view, security is the biggest concern associated with IP addresses. Static IP addresses are easily trackable (after all, they always stay the same). Hackers can more easily compromise them and move horizontally across the network to target other digital assets. This is one reason why security is more than an IT problem, it’s a leadership concern.
- Find out why network security matters to C-suite executives. Read the blog.
After more than 30 years working with remote industries, we believe in security-first design for devices and networks. This means taking a zero trust approach – “never trust, always verify” – in IIoT devices.
Let’s look at three possible security threat examples.
Scenario #1: The Outside Contractor
An oil and gas company hires a systems integrator or contractor to service equipment and handle diagnostic repairs. The contractor and their team remote in, having access to static IP addresses. Now, they can remote anytime (yes, even through a firewall). It is invited risk from the outside. With zero trust, we can put a time window (let’s say 1 PM to 5 PM) that day, offering up no IP address for a DDoS (distributed denial of service) attacker to hammer the system, freeze assets, and crash the network.
Scenario #2: Disgruntled Employee
An internal employee of a smart agriculture company is upset. They’ve been downsized, but it takes time for IT to restrict permissions. The employee knows the IP addresses of devices on the network and can attack the network, steal information, and shut down the business. Using zero trust, permissions can be removed.
Scenario #3: The Onsite Contractor
Onsite contractors pose a different threat. They can put the IP addresses on their business server and move horizontally. This is one reason VPNs are vulnerable. Once a dark actor is in, they have access to everything inside the network. Zero trust locks every device and grants the contractor permission to only areas of the network they need to access.
Unplanned downtime is a fallout from security breaches.
What are the costs of downtime? According to a 2022 report by Siemens, for example, the cost of downtime in oil and gas had doubled in the previous two years to $500,000 per hour. The report says that an average large industrial plant “loses 25 hours per month due to unplanned downtime – more than a full day’s production.” Poor equipment maintenance, security breaches, supply chain issues, and equipment failure can all contribute to unplanned downtime, however, security is the greatest of all these risks.
The Day We Hacked a Customer
The previous scenarios show why exposed IP addresses are important. In addition, here’s a true story of how we hacked into a customer network (by invitation, of course).
The problem: Modbus RTU over serial failed to transmit data across the cell router. So, we immediately examined the cell router configuration. A look at our conversation:
Us: Do you have an IP address?
Them: Yes, but it’s private.
Us: What’s the address?
Them: Here it is.
Us: We’re in your router.
Them: What??? How??
In a matter of seconds, we were in their router. We could have made modifications, identified their radio settings, changed usernames, changed passwords – and they never would have gotten back into the network other than through the factory default.
So, is a private IP address really private? What makes it private? Have you tested it? Are you 100% confident it is secure?
Here’s the thing: even though the customer locked down the router, they didn’t lock down the devices connected to it. That’s a common problem. As you’ll read in the next section, not knowing what devices are secure is made more serious because of public IPs and port forwarding.
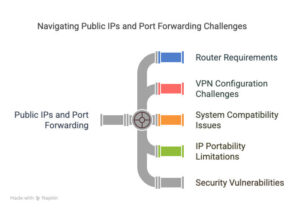
Public IPs and Port Forwarding
If you like taking the hard road, you’re in luck. Port forwarding is the typical path to overcome static IP shortcomings.
It’s a messy one.
Port forwarding redirects network traffic from a specific port to a device. Anytime an IP address goes over the internet, it becomes a public IP, which comes at a cost by the ISP. Based on a blog by Lightyear, ISPs rented public IPs by the block at around $0.06 per IP or $15.36 per month. By 2022, the cost had risen to $0.55 per IP or $140.60 per month. If you have 100 devices, public IPs add up. Some public IPs are not portable and not transferable from carrier to carrier. Some systems do not support port forwarding IPs. Some SCADA systems allow static, but not port forwarding IP addresses.
A remote industrial enterprise constructed over time has a network with many systems, devices, and platforms. Each device’s static IP address is an invitation for a security breach because they are open to anyone from the outside world.
Port forwarding static public IPs is an option, but at what cost?
FreeWave Solves the IP Dilemma
FreeWave’s Elements™ ES1000 is an IIoT security appliance for remote assets, bringing together FreeWave’s lineup of industrial end-to-end IIoT hardware and software solutions and services.
ES1000 secures IIoT networks with out-of-the-box, plug-and-play software, providing a secure cellular connection to the internet. ES1000 features a built-in zero trust security service called Zentry™, an agile software solution also offered as a standalone software license for those with existing cellular gateways already in the field.
Zero trust solves the IP dilemma because it is point-to-point security – no matter how many points are added to your network. Unlike traditional IP-based security, ensuring protection between individual points in a network means each connection is verified and secured directly. This eliminates vulnerabilities tied to trusting an entire network based on IP addresses.
At the technology level, ES1000 is a workhorse for continuous connectivity and security:
- No cellular-provided IP required
- “Never trust, always verify” least privilege access and micro-segmentation
- All IP addresses look static and are secure
- No port forwarding required
- Automatically patches security holes in realtime
- IPs are portable across (up to) 600 global carriers in realtime
- No configuration needed
- Integrates with SCADA systems
- Easy device management
- Micro-segmentation ensures the right people view the right things and nothing else
- Simple to install and maintain
- Can be integrated into any networks
- Invisible to the outside world
What do you think?
Static IP addresses have long been used by enterprises to connect remote devices to a network, including VPNs. However, you can’t protect what you can’t manage. Many industrial operators don’t have a deep IT bench, but that’s OK. Midsize organizations are fully capable of recognizing security holes in a network before outsiders do.
Do you think static IPs are a liability in the industrial space? Are your IIoT devices designed to overcome cybersecurity threats? Is your point-to-point connectivity secure?
At FreeWave, we believe in simplifying IIoT. Modern remote industrial operators need flexibility, ironclad security, digital resilience, and seamless reliability – without complexity.
To learn more about how FreeWave can help secure your network with the ES1000 security appliance, talk to a FreeWave IIoT expert. In the meantime, download the Top 5 Questions to ask about your IP addresses.